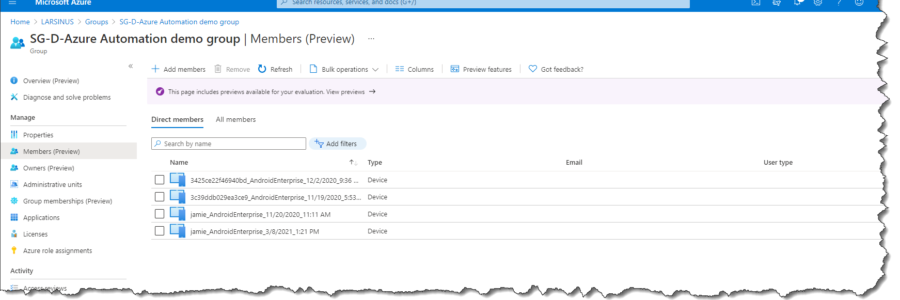
Create dynamic AAD group based on Intune object properties
When creating your dynamic device Azure AD groups for use with Intune, you are limited to set of properties found on the Azure AD object. But what if you wanted to have a group based on properties you only find on the Intune object? What if you want a group based on ‘Android Security Patch Level‘? Turns out we can do that by having a little fun with Microsoft Graph.
I’ve had a few customers asking for this and read about others asking for it too. So, I decided to see if it could be done in a reasonable way. Started looking at the Graph API for groups and saw it was a couple of ways to add/update an AAD group with new members. From my testing I found out that the syntax for just adding one member didn’t work. But the syntax for adding multiple was working fine, so I decided to go for only that. Having an array with only one item works in the same way as with multiple items.
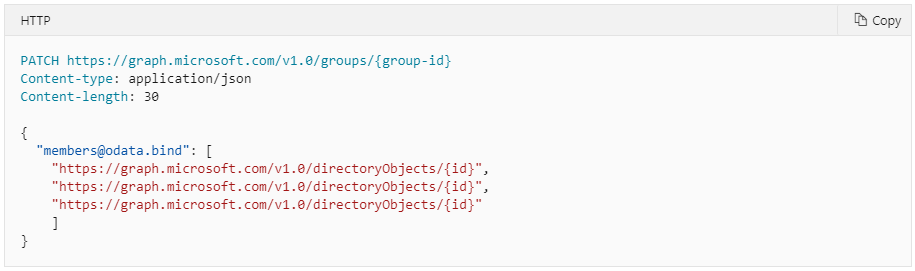
Azure AD dynamic group limitations
Instead of being limited to these AAD object properties:
accountEnabled, objectId, displayName, isRooted, deviceOSType, deviceOSVersion, deviceCategory, deviceManufacturer, deviceModel, deviceOwnership, enrollmentProfileName, managementType, organizationalUnit, deviceId, devicePhysicalIds, systemLabels
You can now create “dynamic” AAD group based on these Intune object properties:
id, userId, deviceName, managedDeviceOwnerType, enrolledDateTime, lastSyncDateTime, operatingSystem, complianceState, jailBroken, managementAgent, osVersion, easActivated, easDeviceId, easActivationDateTime, azureADRegistered, deviceEnrollmentType, activationLockBypassCode, emailAddress, azureADDeviceId, deviceRegistrationState, deviceCategoryDisplayName, isSupervised, exchangeLastSuccessfulSyncDateTime, exchangeAccessState, exchangeAccessStateReason, remoteAssistanceSessionUrl, remoteAssistanceSessionErrorDetails, isEncrypted, userPrincipalName, model, manufacturer, imei, complianceGracePeriodExpirationDateTime, serialNumber, phoneNumber, androidSecurityPatchLevel, userDisplayName, configurationManagerClientEnabledFeatures, wiFiMacAddress, deviceHealthAttestationState, subscriberCarrier, meid, totalStorageSpaceInBytes, freeStorageSpaceInBytes, managedDeviceName, partnerReportedThreatState, deviceActionResults
Either use an existing Azure AD group or create a new one.
The membership type must be ‘Assigned”
Solution
I could write a PowerShell script, and then manually run it from time to time. That would work, but it wouldn’t be very dynamic. By leveraging Azure Automation with a runbook and a schedule this would be fully autonomous. How to set up an Azure Automation account and create an Azure App Registration is described partially here ‘custom reporting’ blog and reviewing the step-by-step guide in the GitHub repository and in more detail in this GitHub repository.
If you don’t have an Azure App, go to the Azure App Registration blade, and create one. Remember that the app secret is only visible when you create the app. Save it in a secure place.
Then create your Azure Automation account.
In my lab I reuse the same Azure App and Automation account from the ‘Intune custom reporting’ blog, but in a real-world scenario, I would recommend creating a new app and account for this purpose.
When that’s done, you can create a new runbook and just copy/paste the PowerShell script I’ve uploaded to my GitHub repository.
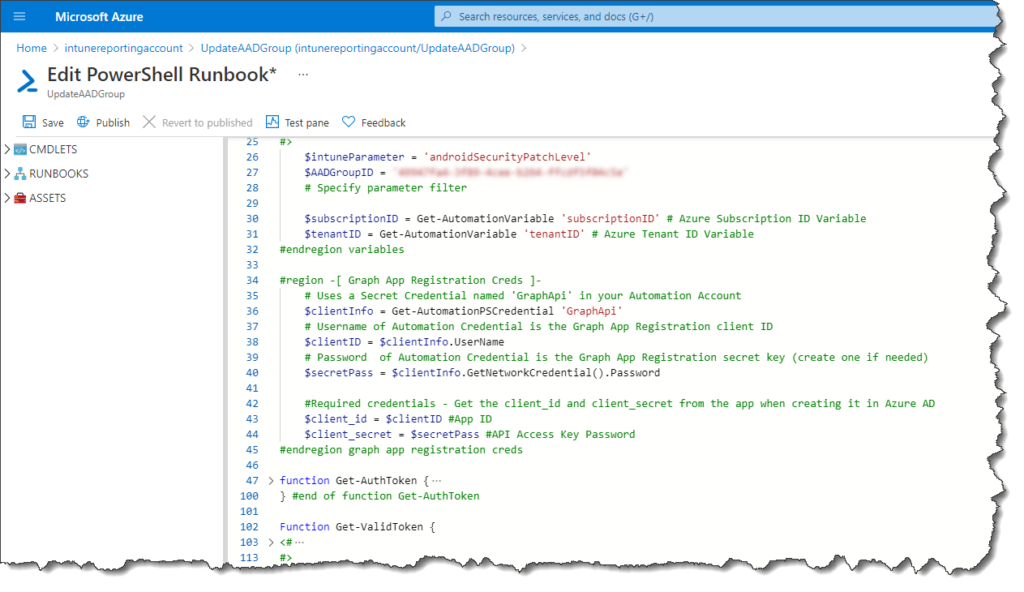
In the first section (down to line 45) I define the variables. You need to create the variables in your Azure Automation account where you see it uses the ‘Get-AutomationVariable‘. Again, this is explained in the GitHub step-by-step guide.
There are three lines you can/need to change in the script (line numbers may change…).
Line 26 – $intuneParameter = <specify the name of the property you want to validate against>
Line 27 – $AADGroupID = <add the Group ID of your Azure AD group you want to use>
and…
Line 223 – if ($MDMobject.$($intuneParameter) -eq ‘2020-09-01‘){ –>> change the comparison operator to what you need and the value.
Comparison operators: -eq / -ne / -gt / -match / …. etc.
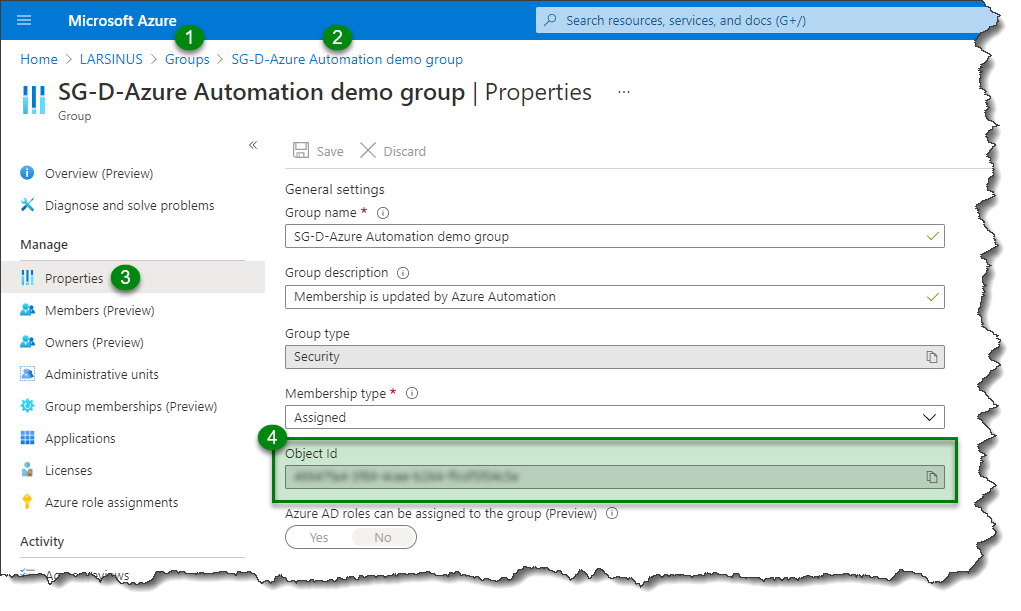
To find the Group ID, go to Azure AD/groups/<your group>
Click on ‘Properties’ and copy the ‘Object Id’
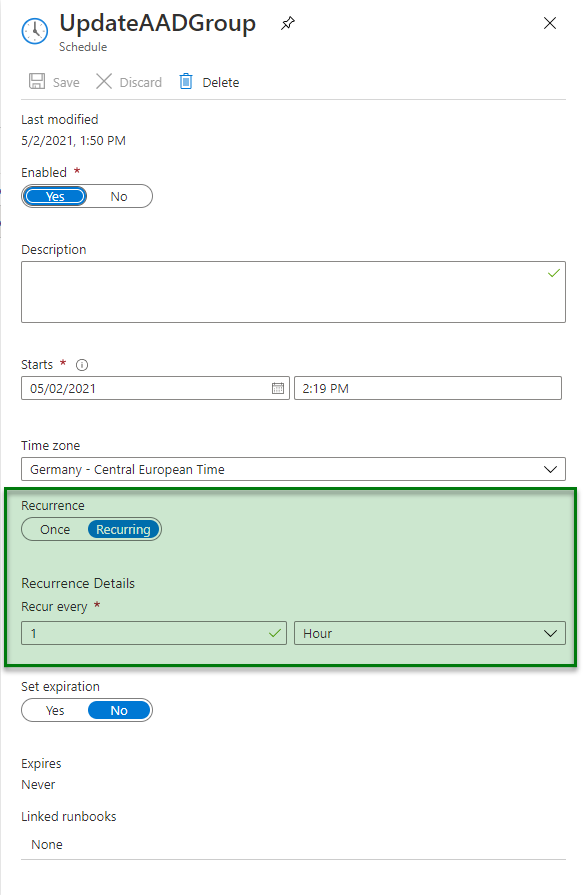
Update frequency
Now create your ‘schedule‘ in the Azure Automation account. The most frequent you can update is once every hour.
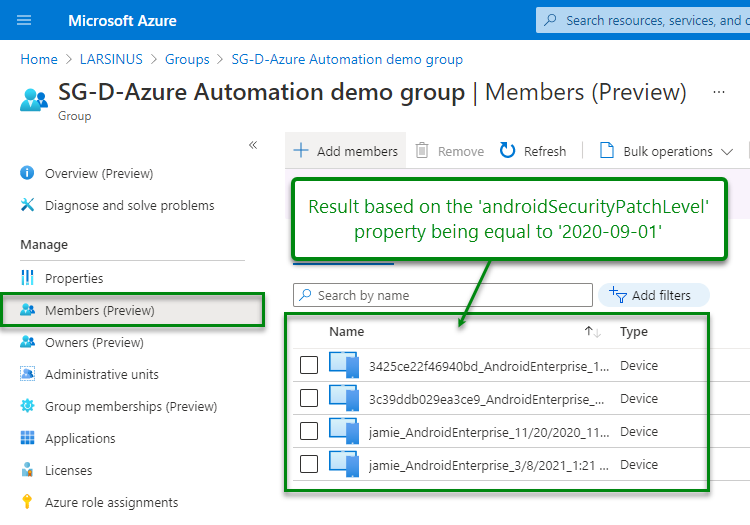
Result
The script will update your group with the devices matching your criteria and remove any device that doesn’t. Devices that previously matched your criteria and added to the group will be evaluated during each update and removed if they no longer match it.
Links
- Graph API Groups | https://docs.microsoft.com/en-us/graph/api/group-post-members?view=graph-rest-1.0&tabs=http
- GitHub step-by-step guide | https://github.com/phmehta94/IntuneAutomatedReporting
- GitHub update group script | https://github.com/larsinus/Public/blob/master/Intune/Update-AADGroupMembership.ps1
- PowerShell comparison operators | https://docs.microsoft.com/en-us/powershell/module/microsoft.powershell.core/about/about_comparison_operators?view=powershell-7.1
- Azure Automation account | https://docs.microsoft.com/en-us/azure/automation/automation-quickstart-create-account
- Azure App Registration | https://docs.microsoft.com/en-us/azure/active-directory/develop/quickstart-register-app
