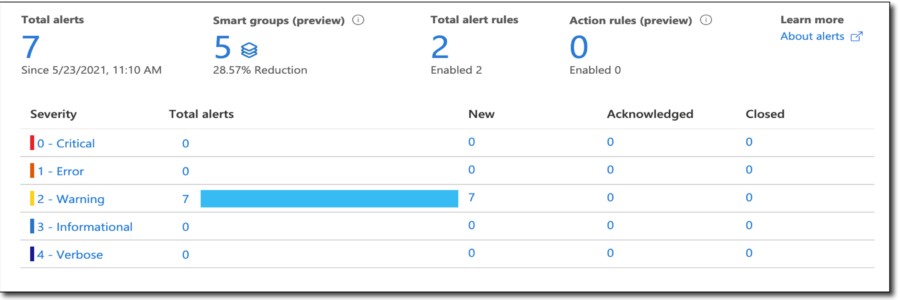
Get notified when your configuration policies change.
You have created your configuration profiles in Microsoft Intune and have successfully gone through your test, and pilot phases. Now you put it into production. Once done, you don’t want it to change (most likely) unless it’s been approved by your Change Advisory Board (CAB). I’m a fan of having a good naming standard which means I rename my policies from “DEV-xxx” to “PROD-xxx” when I put them into production. Any change to such a policy should go through the normal change process.
However, accidents/unintentional changes happen.
If that happens, I would like to get notified. Using Log Analytics together with Intune you can achieve this. Let’s look at how.
Scenario
My starting point is that I already have a configuration profile that has been put into production – “PROD-Email profile”. Then someone changes the setting for calendar sync from ON to OFF.
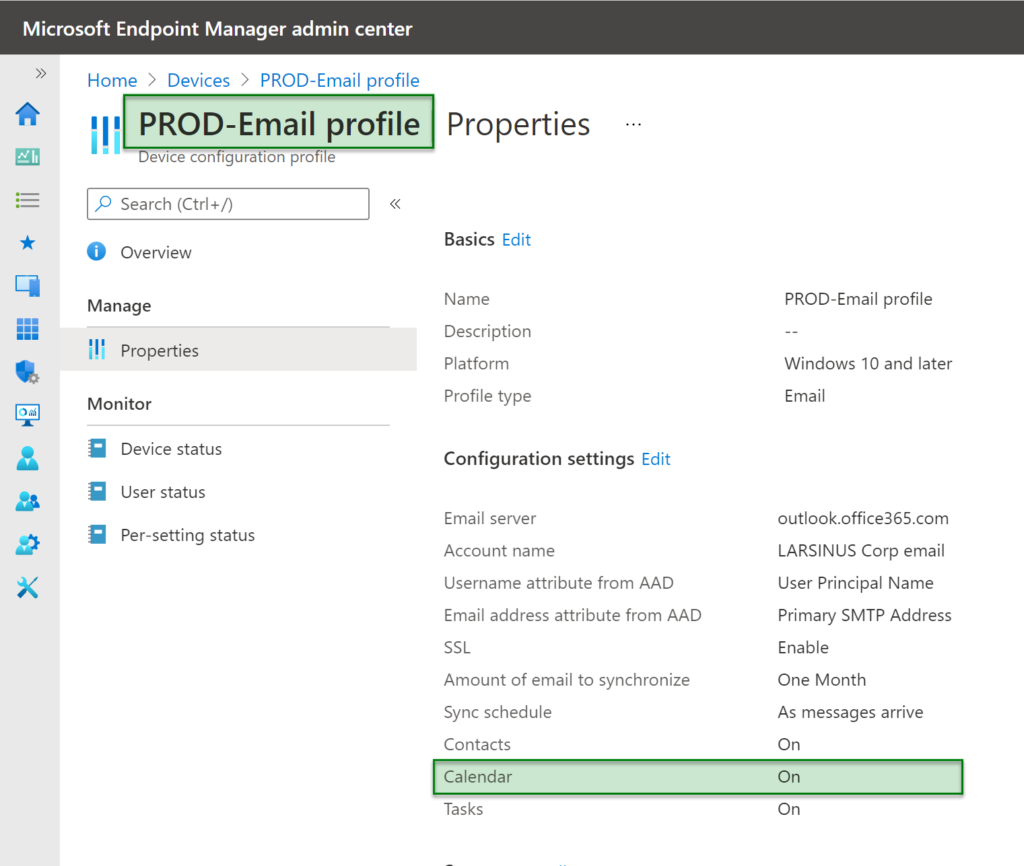

The IT department would figure this out eventually. Either by reviewing the policy, users complaining or by the number of support tickets regarding calendar sync not working… Not ideal.
Create change filter query in Log Analytics
If we navigate to Log Analytics, <your workspace>, Logs, LogManagement, and finally IntuneAuditLogs.
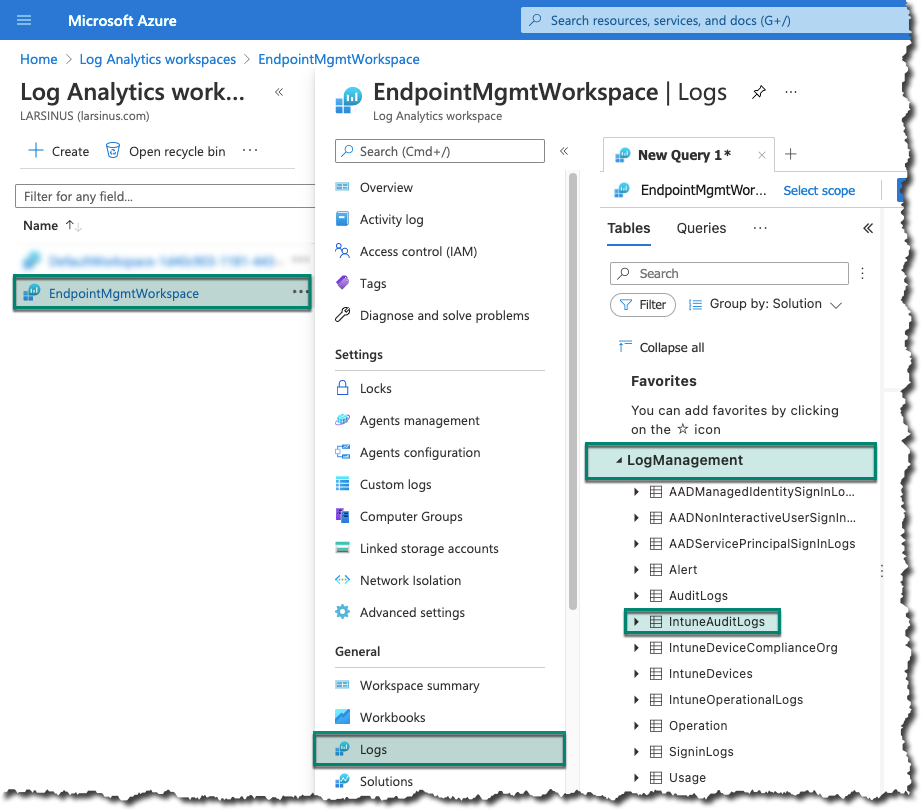
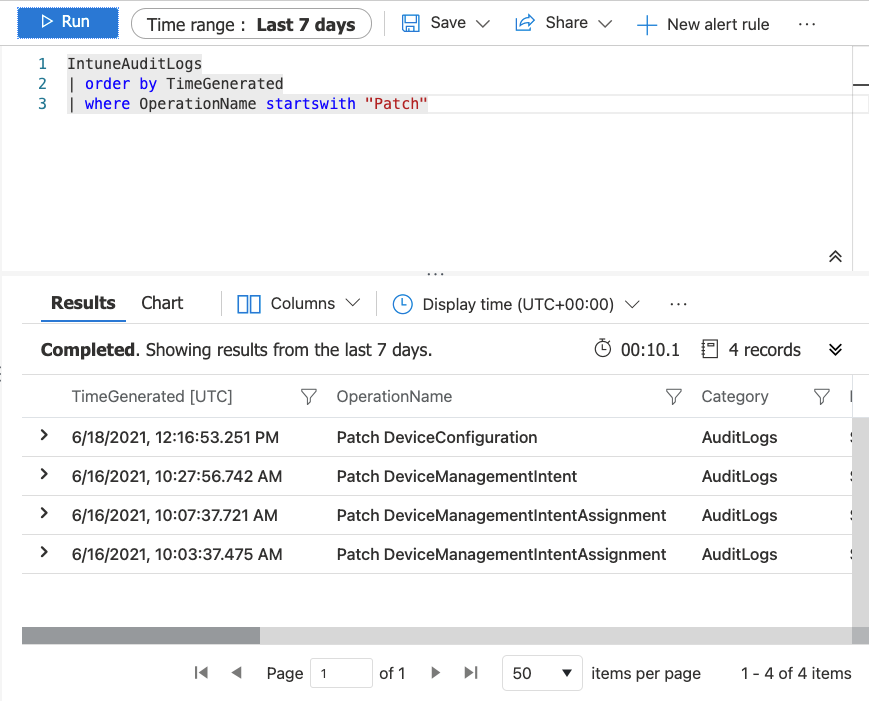
You can either start typing in the query windows or just double click on the ‘IntuneAuditLogs’ table. If you double click on it, it’ll auto type it for you. Depending on the ‘time range’ you use, you’ll get a list of operations done in your environment. When looking at the different operations you can see that ‘Patch’ is used for changes. Now, we have a list of all the changes that has happened.
But I only want to see changes to my policies that starts with ‘PROD-‘.
The easiest way of doing that is to expand one operation and browse down to ‘TargetDisplayNames’ and click on the three dots and then click on ‘Include ….’
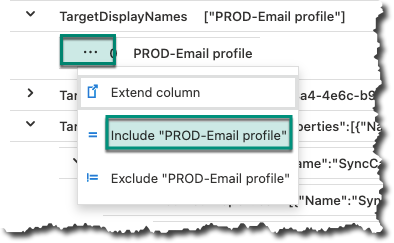
Now, change the query from being equal to only start with ‘PROD-‘ to pick up changes to all policies using this naming standard.

The challenge with this query is it will notify you when someone put a new policy in production as well.
Example:
Renaming a policy from ‘DEV-Email profile’ to ‘PROD-Email profile’
To avoid getting notifications for those type of changes we need to add another section, like in the query shown below.
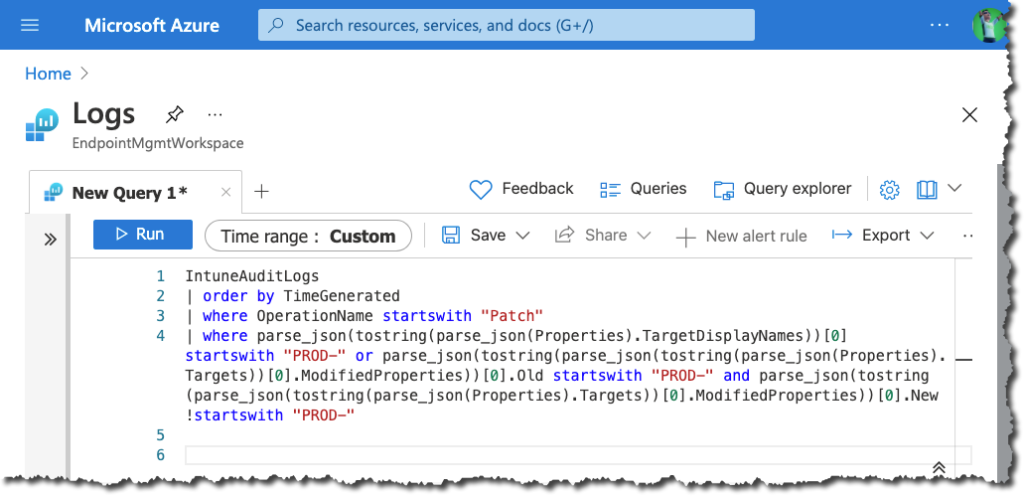
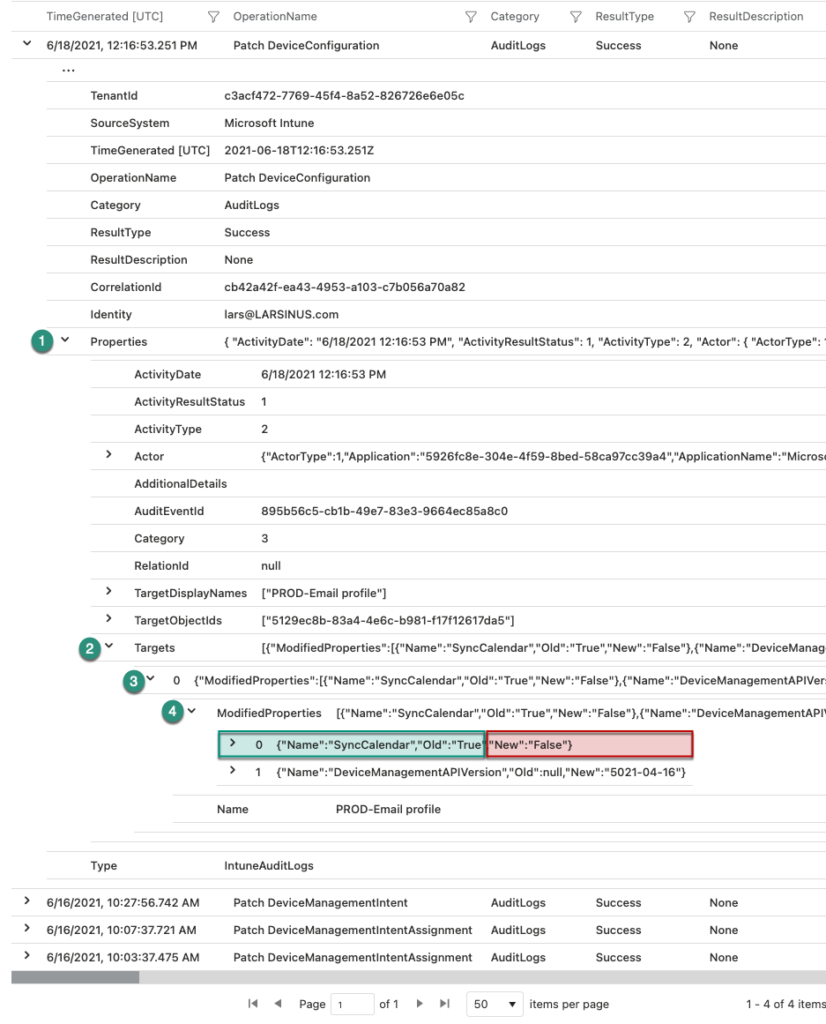
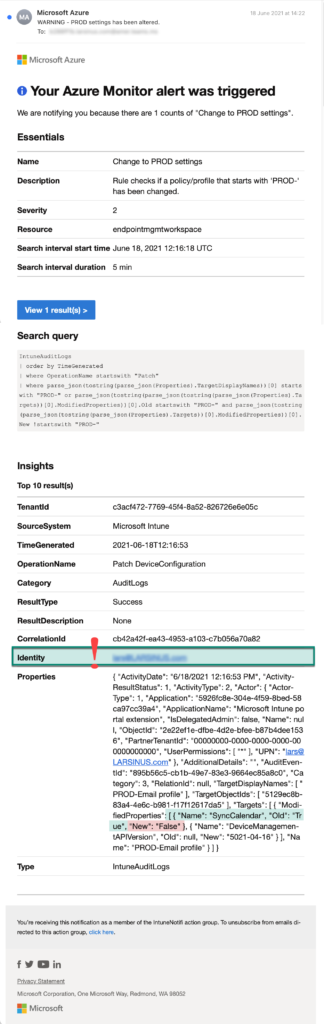
When a change now occurs, you can use that query to view which was changed and what was changed. In our example we changed the calendar sync in our email profile. The image below shows that change (4). Expanding ‘ModifiedProperties’ shows the name of the property that was changed (‘SyncCalendar’), the old value (“Old”:”True”), and the new value (“New”:”False”).
Create alert rule
Now that we have our filtering rule, we can create the alert rule.
Still in Log Analytics, scroll down to ‘Alerts’ and click on ‘New alert rule’.
When creating a new rule, there are three different sections that need to be populated. The ‘Scope’ should already be filled out in our case. If not, select a workspace.
In the ‘Condition’ section we need to select a ‘Signal type’, ‘Monitor service’, and ‘Signal name’. When clicking on the ‘Signal name’ link it’ll open another pane where we need to add our filter query, alert logic, and evaluation frequency.
Select ‘Log’ as the ‘Signal type’, ‘Log analytics’ as the ‘Monitor service’, and ‘Custom log search’ as the ‘Signal name’.
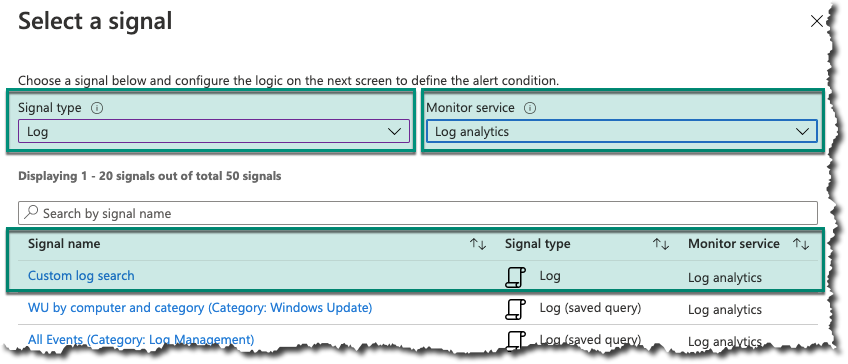
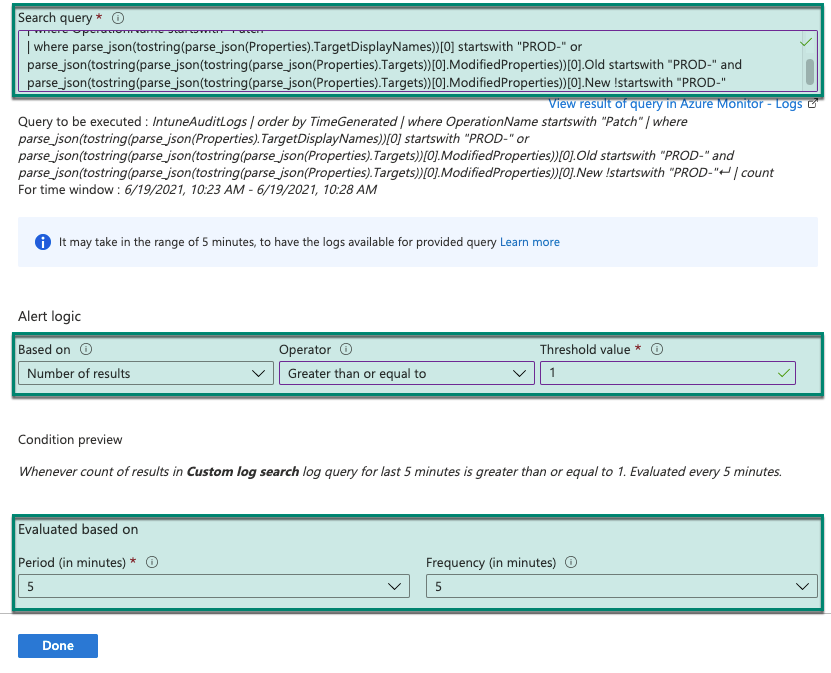
Paste the filter query we created in the ‘Search query’ window.
‘Set the Alert logic’ properties using these values:
Based on = ‘Number of results’
Operator = ‘Greater than or equal to’
Threshold value = 1
Specify the ‘Evaluation’ frequency to what you want. In my case I’ve set to check every 5 minutes for changes done in the last 5 minutes.
Next, we need to create a new ‘Action group’.
Select a subscription and resource group, before giving it a group- and display name.
We have several options for notification, but I’ve selected email and SMS in my example as shown below.
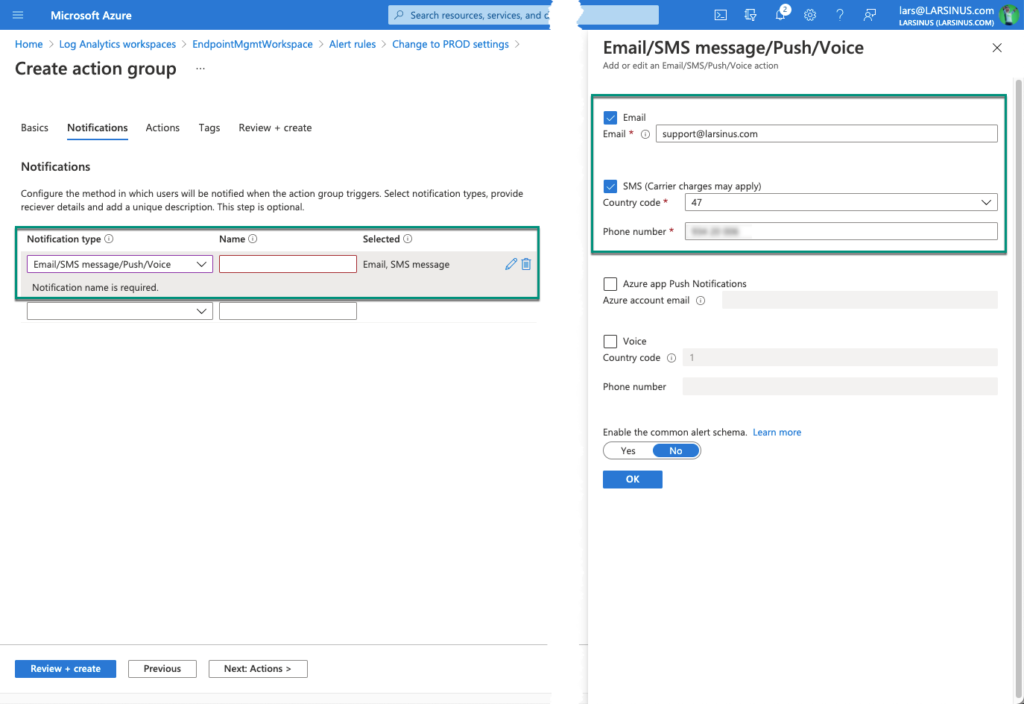
If you want to can also add some actions to run if this alert is triggered. The options are ‘Automation runbook’, ‘Azure function’, ‘ITSM’, ‘Logic app’, ‘Secure webhook’, or ‘Webhook’.
Apply tags to your resources and resource groups to categorize and organize them logically into a taxonomy. Each tag consists of a name and value pair. Learn more about using tags
Then review/create it.
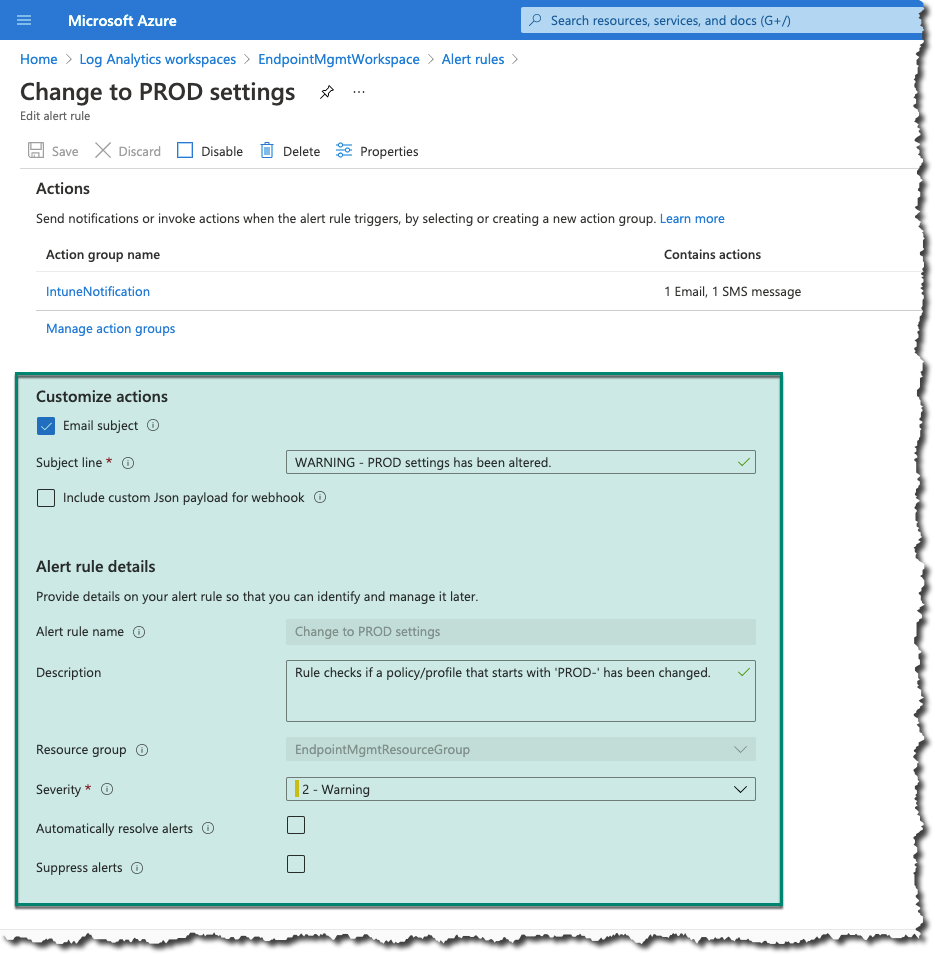
Back to the alert rule page we have a few final settings to configure.
We need to specify the subject line in our alert email, specify the alert rule name, select a resource group, and specify the severity.
Remember to save, and we’re ready to test it.
Result
I’m saving the change (turned off calendar sync) I made to my ‘PROD-Email profile’ policy.
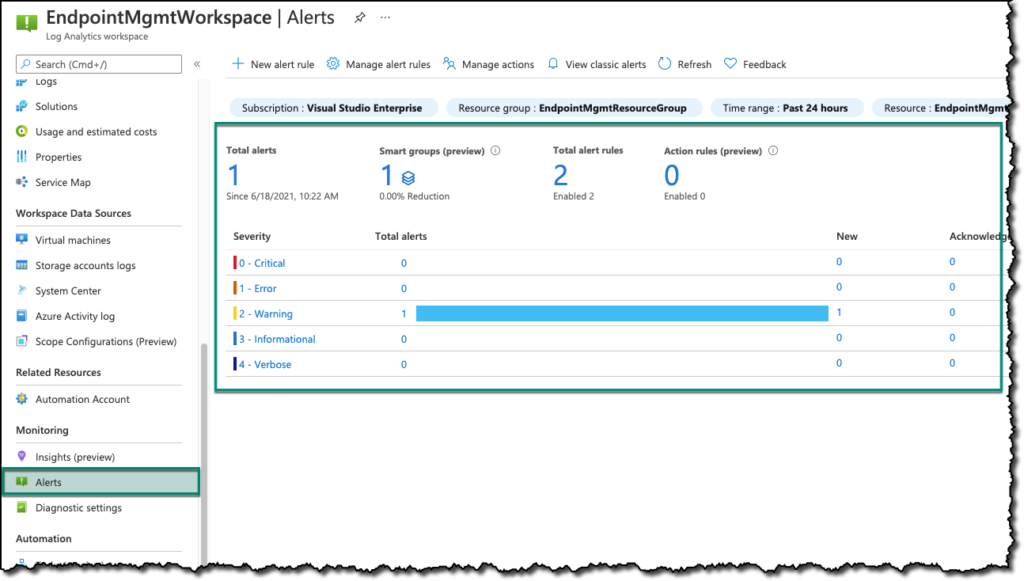
When I’m going back to the ‘Alerts’ section in Log Analytics after waiting for five minutes I see this information screen.
The email notification that’s being sent looks like this. Notice that we see the identity of the account that made the change as well.
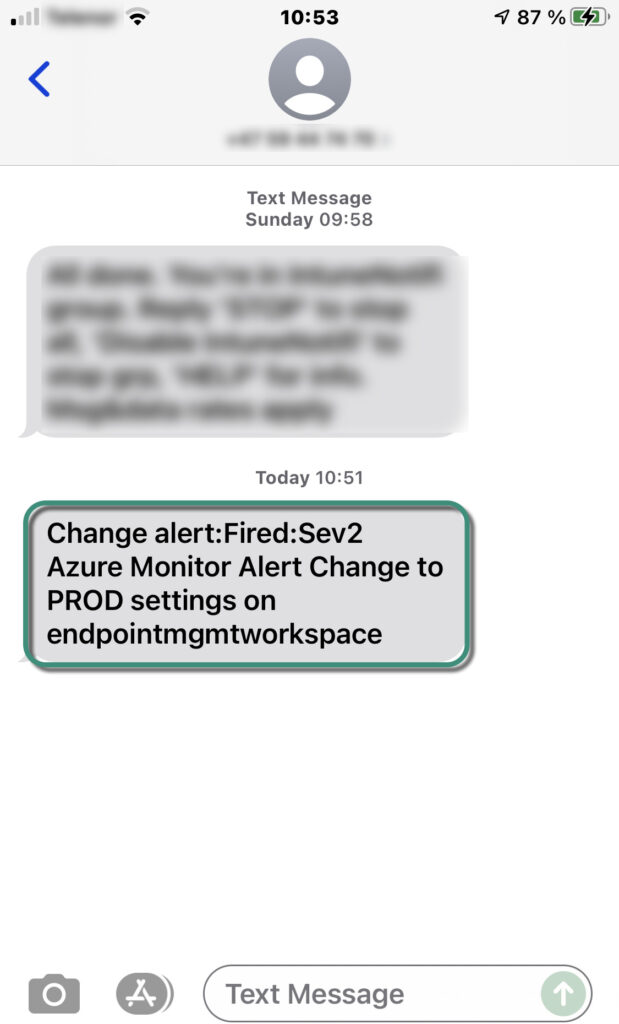
Finally, the text message that I configured to be sent. Maybe not very useful as it lacks the detailed information you get in the email. However, you get a notification that something has been changed so you can go to Log Analytics to get the details.
Final note
This is a straightforward way of getting notified if one of your configuration policies get changed. There are probably multiple ways of doing this, but I found this to be sufficient for my use case. You can also use a Teams channel email to send the notification, but the message is by default too large to display, and you end up having to click a link to view the email in your email app/browser.
To get around that you can create a webhook and specify the payload to what you want.
Read the documentation in the ‘Links’ section for all the details of what you can do.
Happy alerting!
Links
- Log Analytics | https://docs.microsoft.com/en-us/azure/azure-monitor/logs/log-analytics-overview
- Webhook actions | https://docs.microsoft.com/en-us/azure/azure-monitor/alerts/alerts-log-webhook
