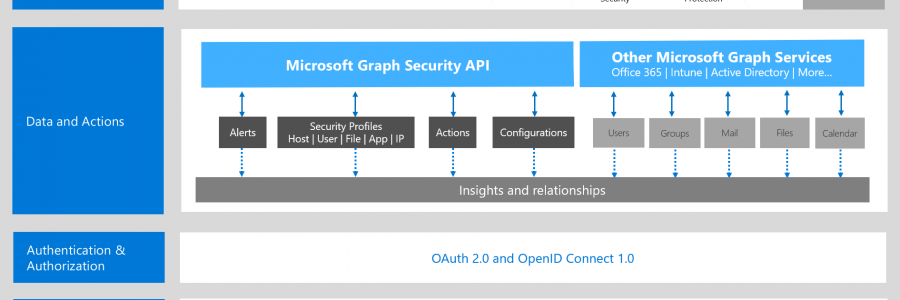
How to use MS Graph from PowerShell … and Graph Explorer
Thought I should write one long post, but I quickly realized it’s too much to cover. So, expect to see more posts on this topic.
You can always go the uncomplicated way and just type “Install-Module -Name Microsoft.Graph.Intune”. That’ll give you – as of now (2020.06.18) – 1569 cmdlets. Nice! However, if you learn to query the Graph directly you don’t need to wait for someone to create cmdlets and you can query a lot more stuff other than Intune!
I would recommend reading the “Getting Started” section on their GitHub as it is especially useful if you want to connect to and leverage Microsoft Graph! Link: https://github.com/Microsoft/Intune-PowerShell-SDK#getting-started I’ll just add a little snippet here for convenience.
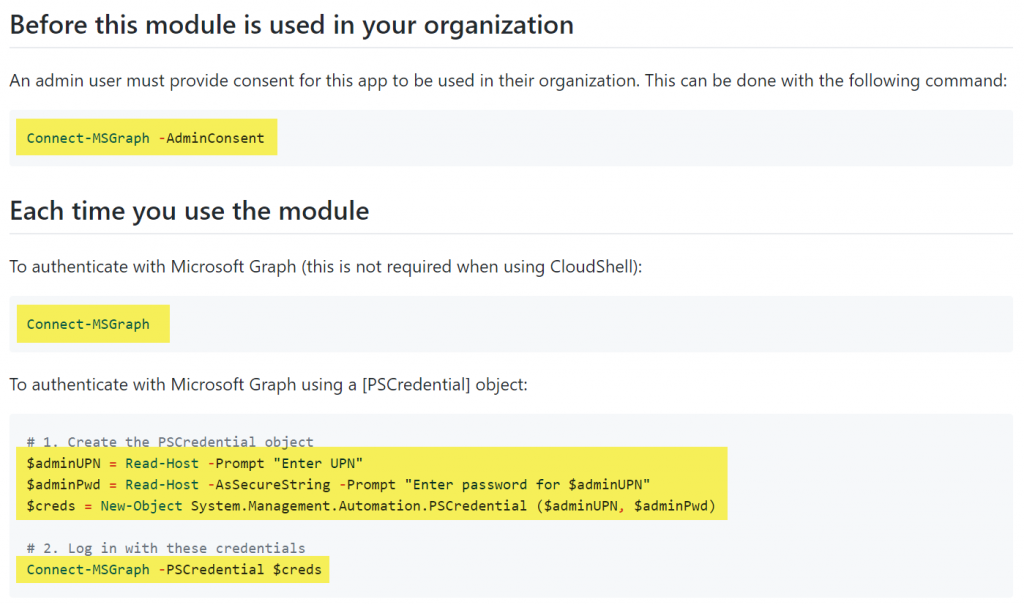
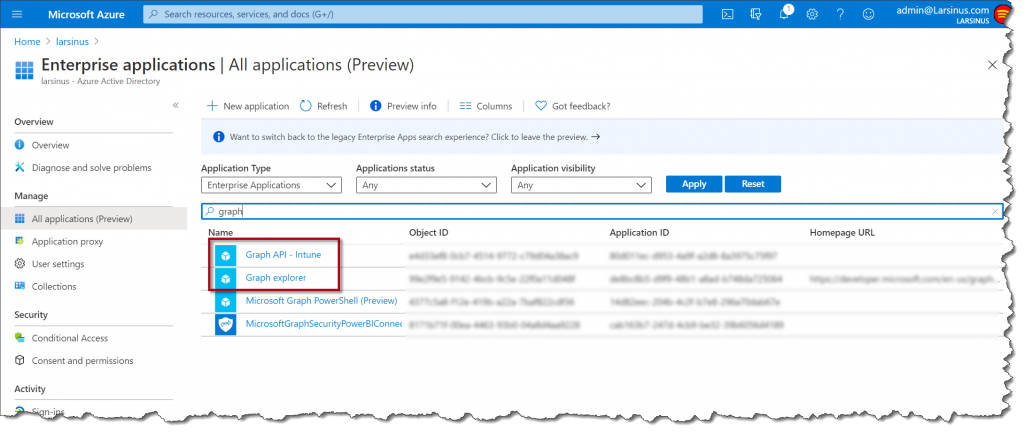
That should take care of allowing you to connect to, and use Graph. It’ll create an application in Azure AD so if you want, you can go there and examine it. Log on to https://portal.azure.com and navigate to “All applications (Preview)” and search for “Graph”. You might have – like me – more than one application. You just need one, but if you do it from PowerShell and from “Graph Explorer” you’ll end up with two.
The Graph Explorer one is just for exploring and testing the graph but you should think of the Application as an endpoint that both provides authentication and also is the interface which grants a token with specific permissions for your specific needs.
So, having a more specific App for a specific need is important. You do not want to allow anyone to do anything over a more general test Application like the one setup for Graph Explorer.
Ref.https://docs.microsoft.com/en-us/azure/architecture/framework/security/applications-services#identify-and-classify-business-critical-applications
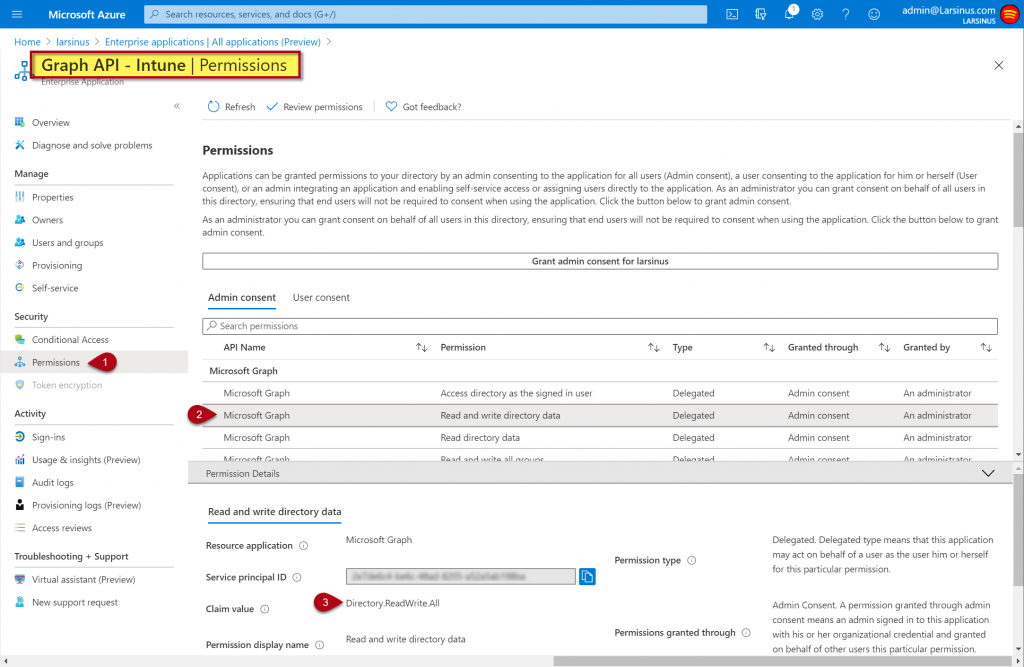
You can click on it to get more details and look at “Permissions” in the left column and then review them in the main window.
You can do the same from “Graph Explorer”. Just navigate to https://developer.microsoft.com/en-us/graph/graph-explorer/preview and click on “Modify permissions” and you should be able to locate the same permissions as in Azure AD.
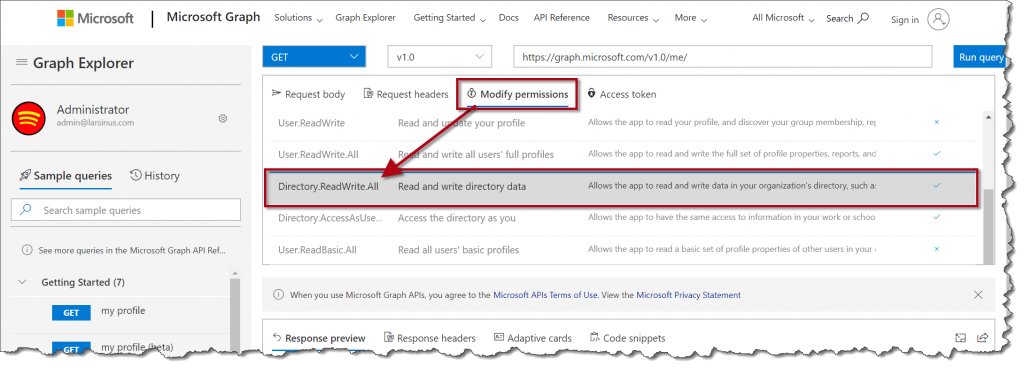
Depending on which API you want to query you might need to edit these permissions. If you head over to the “API Reference” page (https://docs.microsoft.com/en-us/graph/api/overview?view=graph-rest-1.0) and browse to the API you want. You’ll see which permissions it needs. This example is for listing all managed devices (Intune enrolled) in my environment.
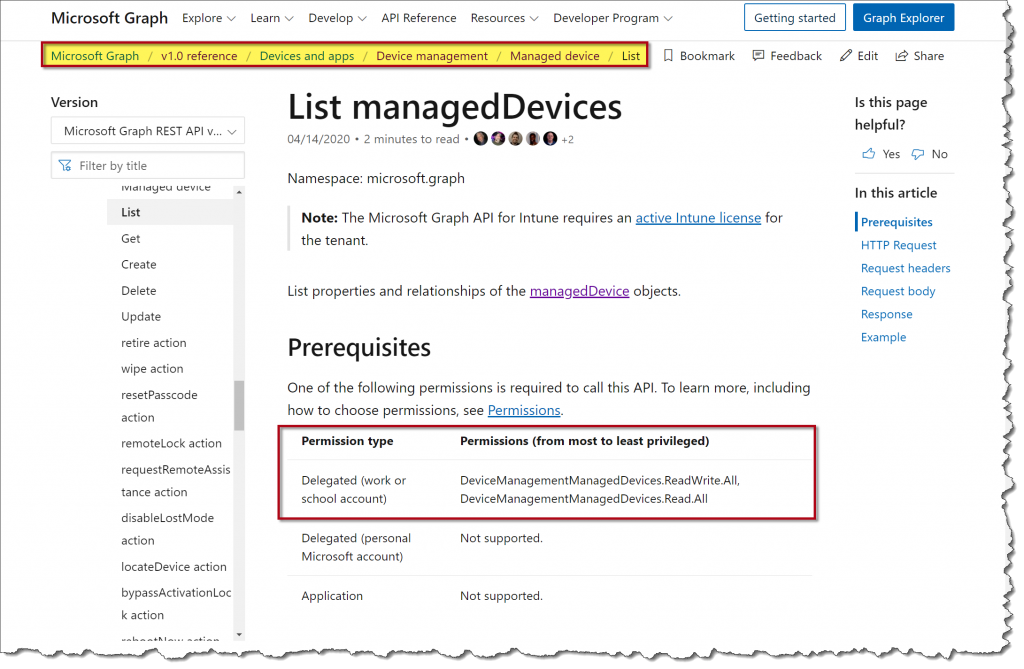
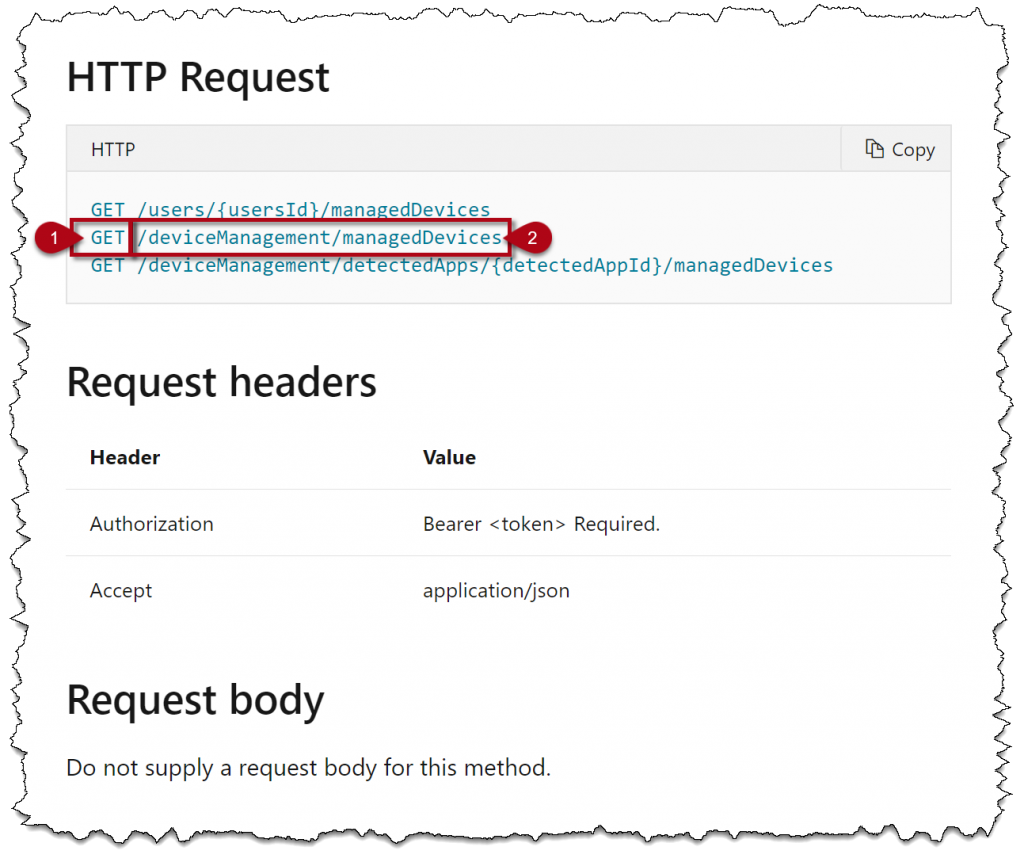
Scroll down a little and you’ll see what kind of HTTP request you need to run and if it requires and any “request headers” or “request body”. In our example we don’t need that. We want to keep it simple for now, but we’ll get back to it later (in another post).
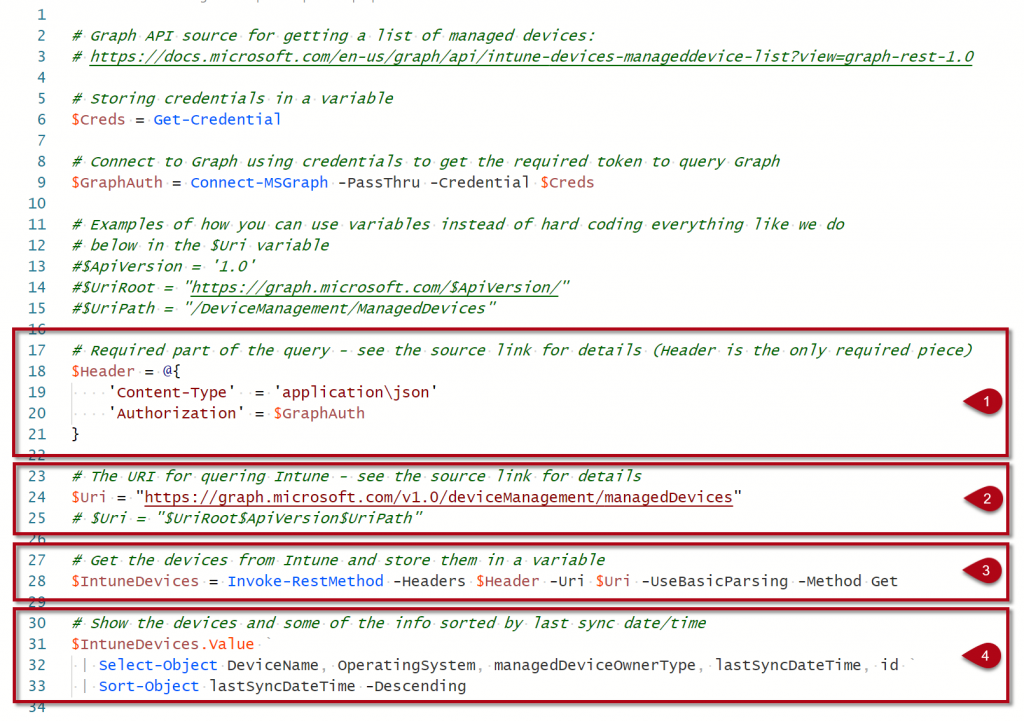
[1] Shows you the method to use, in this case a “GET” because we want to get all managed devices.
[2] is the last part of the “URI” that we need to write in the address field in Graph Explorer. When that is done, click on the “Run query” to get your result as shown below.
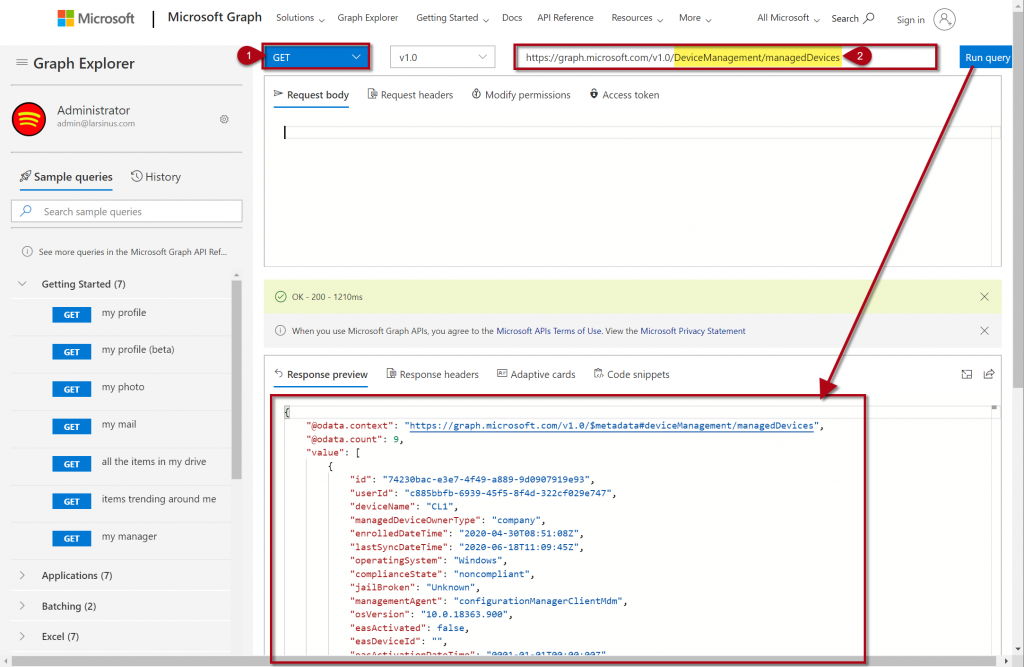
Okay, so now we have figured out the URI and the Request Header and verified it’ll give us the result we want. Now, let’s go to PowerShell and see what we need to do to get the same result.
*** The script is available for download from my GitHub repository (link below in the LINK section)
[1] The required header we saw in the documentation
[2] The URI which we can recognize from Graph Explorer
[3] Is the equivalent of clicking that “Run query” button
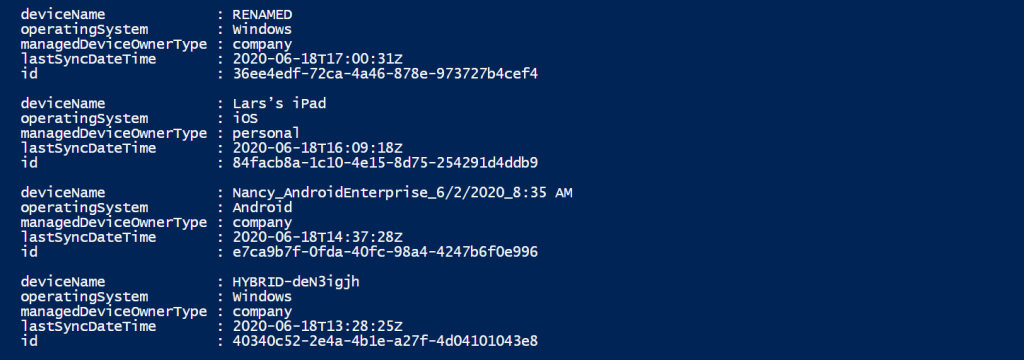
[4] Will list the same result only with a different formatting
Links
- Intune Module GitHub | https://github.com/Microsoft/Intune-PowerShell-SDK#getting-started
- Azure Portal | https://portal.azure.com/
- Microsoft Graph Explorer | https://developer.microsoft.com/en-us/graph/graph-explorer/preview
- Microsoft Graph API Reference | https://docs.microsoft.com/en-us/graph/api/overview?view=graph-rest-1.0
- Script on GitHub | https://github.com/larsinus/Public/blob/master/Intune/Working%20with%20Graph%20-%20Simple%20example.ps1
- Security – Applications and Services | https://docs.microsoft.com/en-us/azure/architecture/framework/security/applications-services#identify-and-classify-business-critical-applications
