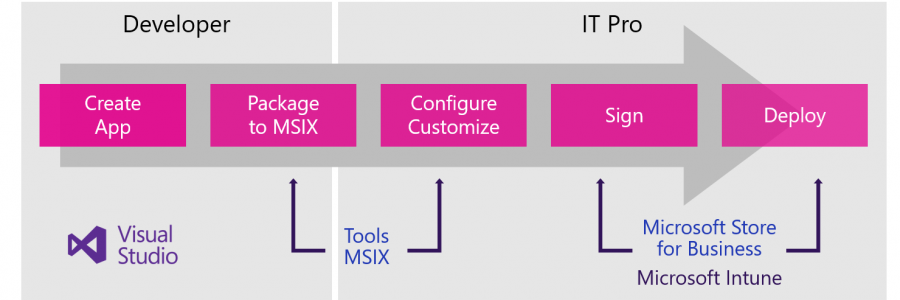
Packaging and signing your .msix package with Device Guard certificate
If you don’t have a PKI but want to start converting your applications to .msix. Then you need a certificate to sign your new packages. Luckily, you have the option to use the Device Guard certificate from Microsoft Store for Business. I created a video to guide you through the process
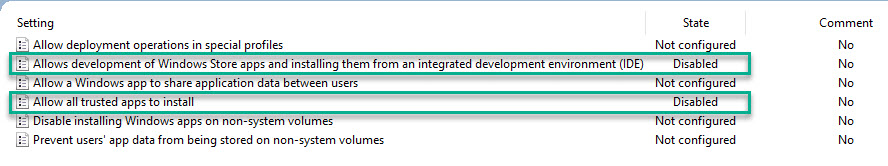
If you play around with it and enable sideloading but then decide to disable it again… That might not be the simplest of tasks…
But I found out that a couple of GPO settings did the trick. Disable these and do a quick ‘GPUpdate /force’ and you’re back to normal.
Download the Enable-Sideloading.ps1 script from my GitHub repository:
https://github.com/larsinus/Public/blob/master/Intune/Enable-Sideloading.ps1
Deploying the app…
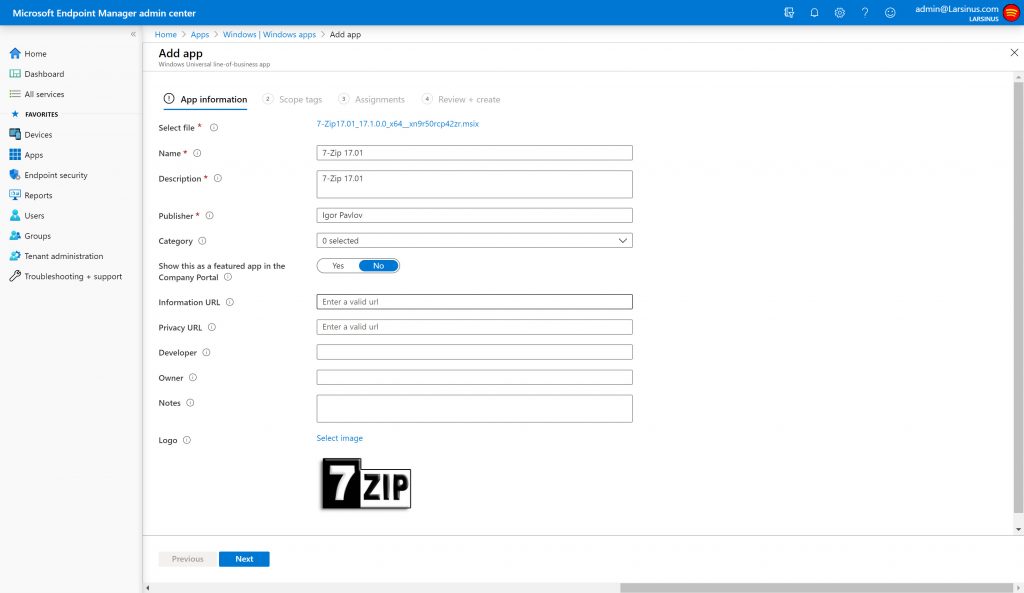
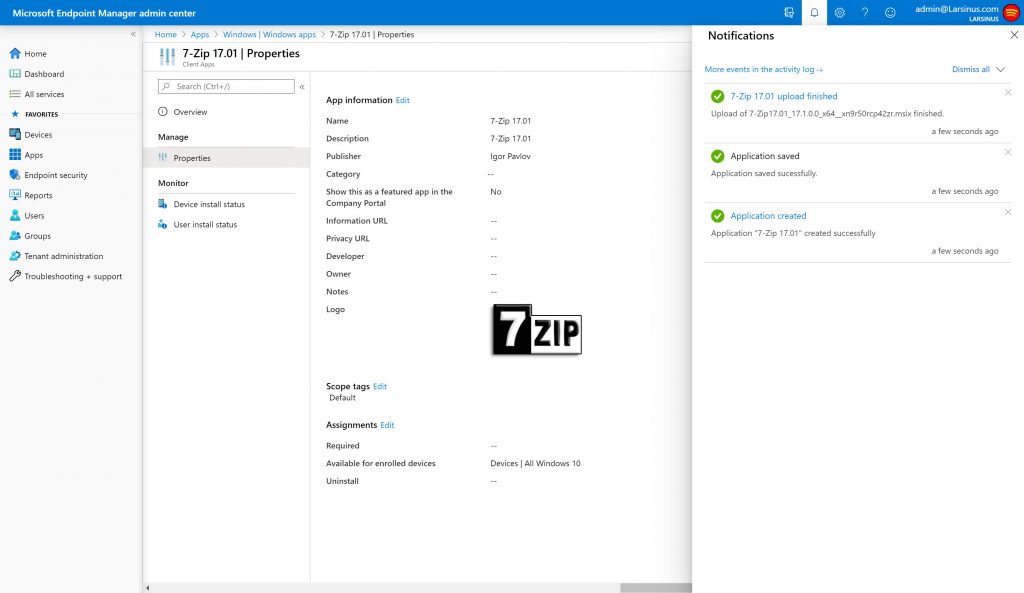
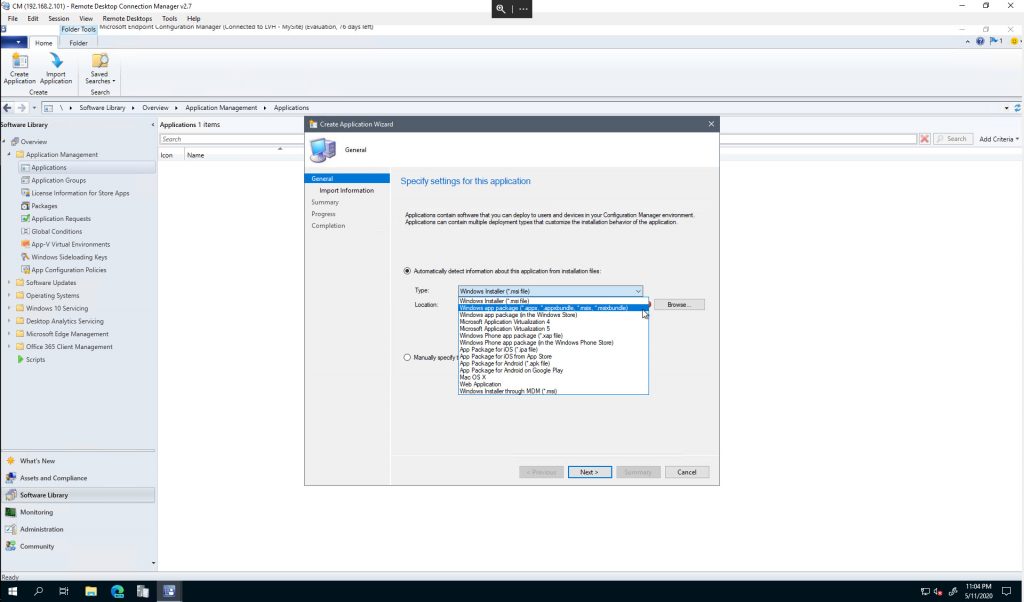
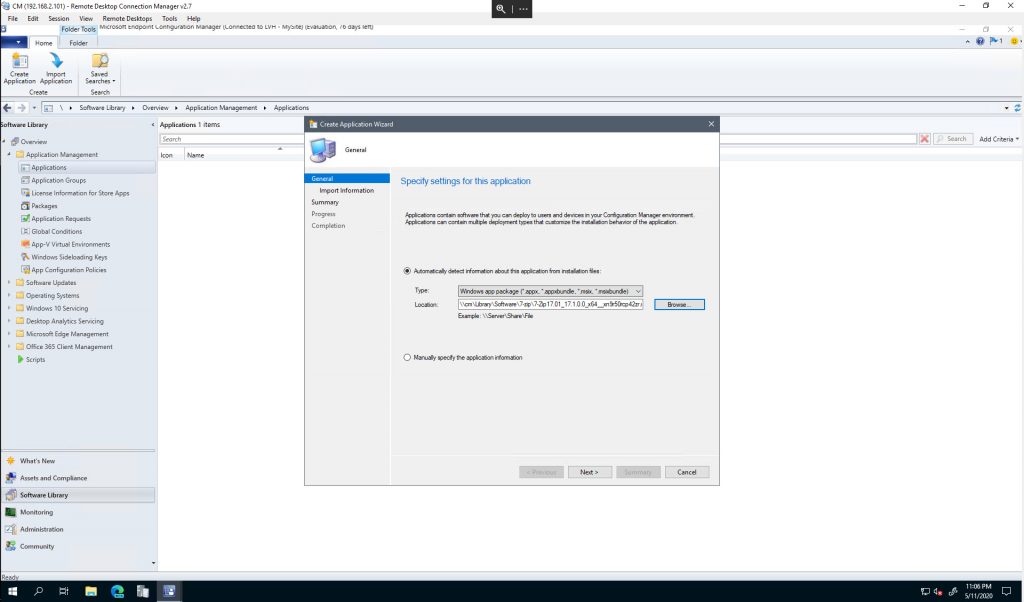
You can use MEM (both ConfigMgr and Intune) to deploy the .msix package.
MEM aka Intune
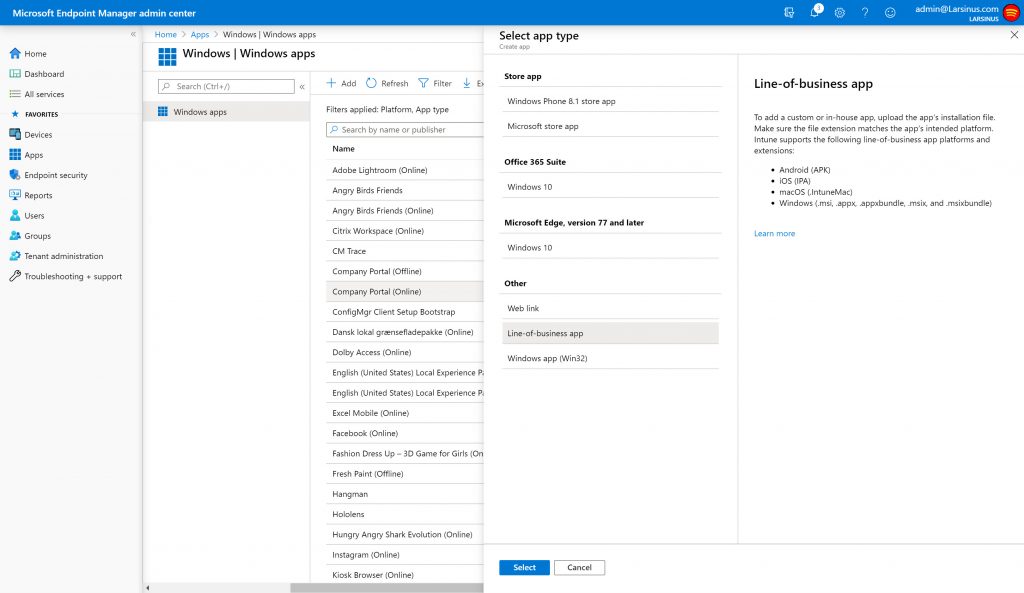
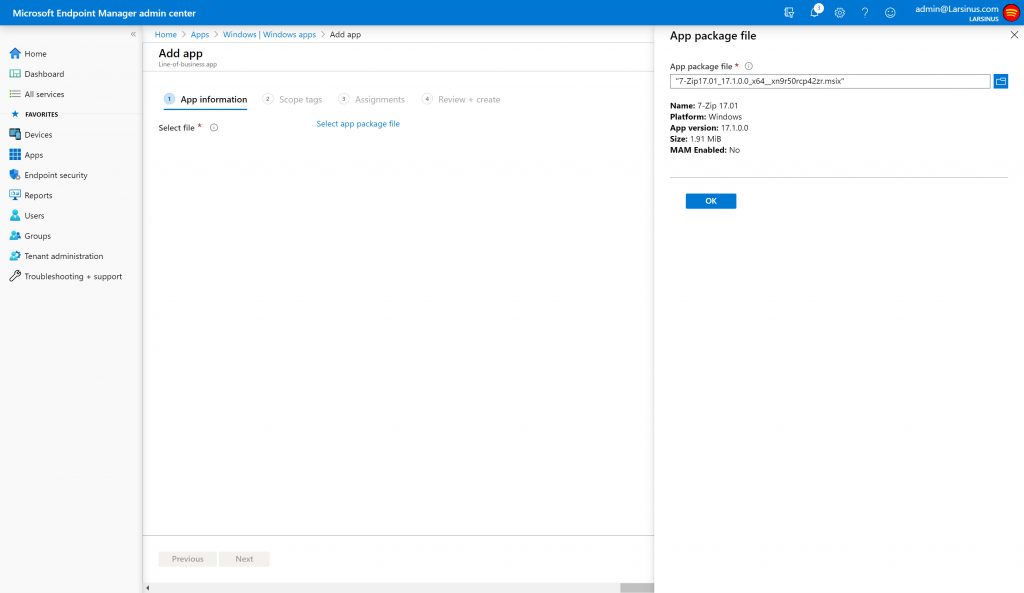
MEM aka Configuration Manager
Have fun!
